I have always wanted a computer that was open enough that it can be inspected for security, and also simple enough that I could analyze it in practice. Precursor is a step towards that goal.
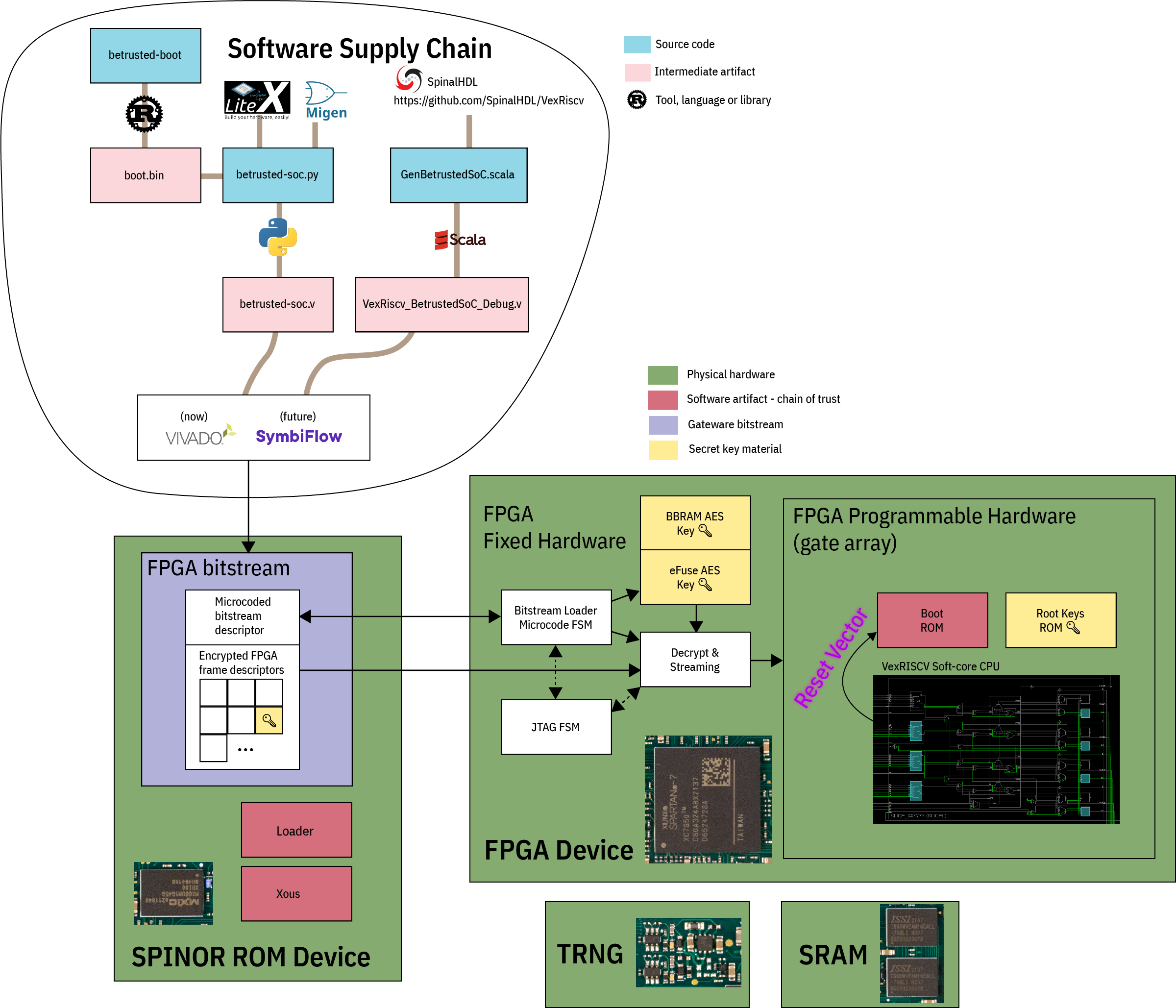
As a test, I made a one hour video that walks through the Precursor tech stack, from hardware to root keys. I feel it’s a nice demo of what evidence-based trust should look like:
The video is a bit of a firehose, so please refer to our wiki for more info, or open an issue to further the discussion.
Erratum #1: I had mistakenly attributed SpinalHDL as a subset of Chisel. SpinalHDL is actually a separately developed HDL by Charles Papon. It was developed contemporaneously with Chisel and inspired by many concepts in it, such as using Scala as the underlying language; but it is not affiliated with Chisel.
Thank you for this fine work
I understand litex/chisel generates verilog.. any reason why this couldn’t then be synthesized/pnr on any fpga? For ex. Lattice/xilinx tools seem to be the vendors of choice.. but what would prevent it from building for Microchip’s SmartFusion2?
Also when using these newer open-source tools, how does one constrain the design , and create test-benches? Can this also done in python/scala, or do you need to use the vendor tool? I’m guessing debugging and single-stepping the risc-v code could use the standard eclipse/open-ocd?
I’m interested in learning fpgas, (either with chisel3 , SpinalHDL , amaranthhdl, etc), any suggestions where to start?
The generic verilog output can target any FPGA, although there is some tuning of the verilog idioms to map better onto the primitives in some architectures (for example in the FIFOs for Migen there is a specific FIFO mode that generates verilog that maps into BRAMs, versus other modes that use distributed RAM).
However, in the case of Precursor specifically, even though everything eventually turns into “verilog”, we make liberal use of direct instantiations of Xilinx hardware primitives as verilog modules. For example, we instantiate the I/O cells explicitly for the SPINOR, because we need intimate control over the input/output delay timings to achieve our target speeds. The Ed25519 block is also specifically coded to take advantage of the Xilinx DSP48E primitives, which contain a “hard macro” multiplier block, allowing us to achieve our performance and density metrics. These can be “unbound” by replacing these models with generic verilog descriptions and then targeting another FPGA family, but you won’t achieve the same performance and density.
That being said, check out Enjoy-Digitals’ “FPGA 101” course:
https://github.com/litex-hub/fpga_101
This is a great starting point.
Hello!
What kind of microscopes are we going to use to inspect the silicon version of Betrusted? On Twitter you said they should be able to show the level of dopant added.
Where one can look up the prices for the fabrication equipment to produce silicon at this scale, is it a 600 nanometer process like Intel 486?
Where is the general discussion happening? Maybe someone has already answered these questions.
What can I do to help you build the precursor? What free or paid work you need help with? I code 24/7 and I’m passionate about this mission of building private tech. I could make you some software, anything. I wanna talk about the possibilities. I can study hardware or software. I will learn and work on whatever needs help none stop. I have a work ethic and really wanna help.
Having been in the tech dev space since Motorola D2 kit days , I really believe that the killer product is – a mobile phone that properly ( ignores , deletes, permanently erases ) any emails , messages , what’s apps from numbers or deliverers that are not in your stored “ trusted communicators enclave “ – you and your network of contacts have the smarts to implement this and I’m on ‘ short finals ‘ but there are billions of users who have to clean spam , trash and take many calls per day from call centres and unwanted advertisers- the pain point is global , and begs a solution – the network providers are like the whores of Babylon and monetise their subscriber lists ! – rant over, but perhaps a super opportunity