Some readers may be aware that I was called upon to perform as an expert witness in a landmark case, USA v. Crippen, where for the first time an individual, Mr. Crippen, was charged with an alleged violation of the criminal portion of the DMCA statute. There have been numerous civil cases over the same statute, but this is the first time that a felony conviction could result from a court case.
As reported by numerous sources, the case was dismissed after the first witness’ testimony. This would be as if two armies brought all their artillery and troops to a border, fired a single shot, and then one side surrendered, realizing that there is no point incurring casualties for a war they cannot win. And thanks to double-jeopardy provision of the US constitution, Mr. Crippen cannot be tried again, since a jury was assembled for his trial. It is a remarkable victory for Mr. Crippen’s defense: as Sun Tzu said in The Art of War, “The best victory is when the opponent surrenders of its own accord before there are any actual hostilities”.
On the surface, it’s hard to appreciate how unique this case is. Not only is it the first of its kind, it’s rare for a US prosecutor to dismiss their case. I’m told that typically, the US government does not go to trial unless they are sure to win the case — they win 90+ % of their cases, with a typical outcome resulting in a plea bargain because of the strong evidence they prepare prior to filing the case. I’m also told that despite the prosecutor’s alleged misbehavior in the case, his pedigree is prestigious (UCLA is a top-15 law school) and his career trajectory is toward a top spot as a judge or politician. And, as I’m learning, neither the prosecution nor the defense leave much to chance in the court of law — so kudos to the defense for educating the judge on terms such as “fair use” and “homebrew”, and applying overwhelming pressure to “crack” the prosecution: a job well done. To be fair, the case was without precedent, so the prosecutor was unaware of basic things, such as the US government’s own guidelines for evidence in prosecuting crimes related to the DMCA. In this case, the US government had to demonstrate that Crippen knew he was violating the DMCA, an element missing from the original evidence but introduced in a surprise statement by the first witness.
However, in a broader legal sense, the trial is a cliffhanger. In some respects, it’s a setup for prosecutors to prepare a stronger, more informed case in the future. Before a case goes to trial, each side must disclose all their evidence and facts to the opposition (and, in fact, part of the reason the prosecution had to dismiss was because they had failed to do just that — it is improper to withhold both exculpatory, and in this instance, impeaching evidence (Giglio v United states)).
As a corollary, the prosecution has a full copy of my prepared testimony. My role as an expert witness is to testify, as an unbiased expert, upon the facts of the case. By dismissing the case before a public hearing of all testimony, the prosecution gets to see the entire roadmap (of which my testimony is a small part) for a defense without its disclosure to the public.
A problem with technology-related cases is that they are never as simple as they seem. The evidence presented by the US government included 150 non-original games in Crippen’s possession, along with two Xboxes that prior to Crippen’s modification, did not play copied games; but, after such modification, they did. As I mentioned earlier in this post, the US government does not go to trial unprepared.
While the true facts are not as simple, raw facts are essentially useless to a jury. The real challenge for me personally was to take a world of technical jargon full of one-way hashes, modular exponentiation, prime numbers, finite fields of characteristic two, stealth sectors, lead-ins, lead-outs, and reflectivity measurements using a laser and a four-quadrant photodetector and boil it down into a set of factually correct statements that any lay jury could not only understand, but feel confident enough to use to decide upon two felony counts.
So, for the purpose of encouraging discussion, criticism, and education, here are some of the key concepts I was to present in the case.
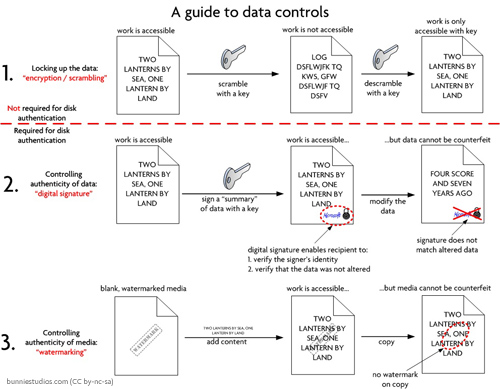
First, it’s important to clarify some basic cryptography terms (click on all images for larger, more readable versions).
The common use of “encryption” or “scambling” is tantamount to an “access control” insofar as a work is scrambled, using the authority imbued via a key, so that any attempt to read the work after the scrambling reveals gibberish. Only through the authority granted by that key, either legitimately or illegitimately obtained, can one again access the original work.
However, in the case of the Xbox360, two technically different systems are required to secure the authenticity of the content, without hampering access to the content: digital signatures, and watermarks (to be complete, the game developer may still apply traditional encryption but this is not a requirement by Microsoft: remember, Microsoft is in the business of typically selling you someone else’s copyrighted material printed on authentic pieces of plastic; in other words, they incur no loss if you can read the material on the disk; instead, they incur a loss if you can fake the disk or modify the disk contents to cheat or further exploit the system).
Simply put:
Relating this back to the DMCA statute:
1201(a)(1)(A) No person shall circumvent a technological measure that effectively controls access to a work protected under this title.
1201(a)(3)(B) a technological measure “effectively controls access to a work” if the measure, in the ordinary course of its operation, requires the application of information, or a process or a treatment, with the authority of the copyright owner, to gain access to the work.
So the first question upon which a jury must deliberate is: given that the document is entirely readable despite anti-counterfeit measures, do these anti-counterfeit measures constitute an effective access control that requires the application of information, or a process or a treatment, with the authority of the copyright owner, to gain access to the work?
To further educate upon that question, it’s important to demonstrate an example of a system where data cannot be accessed, and contrast it to one where it is. The image below compares and contrasts a CSS-protected DVD to the systems used in the Xbox360.
As one can see, on the left, I could access all kinds of images, text, etc. on an Xbox360 DVD. On the right, on the other hand, an authentic DVD secured with a fairly established access control, such as CSS, reads back as gibberish until I can circumvent the scrambling with either a legitimate or illegitimate key.
Now, per the DMCA statute:
1201(a)(1)(A) No person shall circumvent a technological measure that effectively controls access to a work protected under this title.
1201(a)(3)(A) to “circumvent a technological measure” means to descramble a scrambled work, to decrypt an encrypted work, or otherwise to avoid, bypass, remove, deactivate, or impair a technological measure…
So the next question the jury must deliberate upon is, does an Xbox360 optical disk drive (ODD) modification descramble a scrambled work, decrypt an encrypted work, or otherwise avoid, bypass, remove, deactivate, or impair a technological measure?
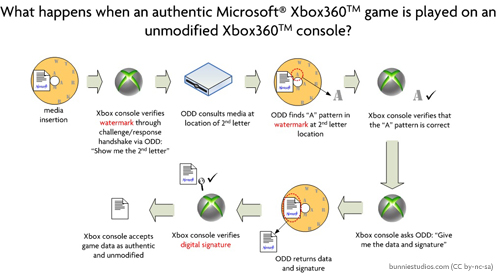
To further education upon that question, it’s important to understand what an Xbox360 ODD modification does; the requisite background to this is “how does an Xbox360 ODD work in the first place?”. Below is a diagram that outlines, in simplified terms, the flow of authenticating an Xbox360 game disk.
As you can see, the ODD is responsible for returning measurements of watermark features (such as reflectivity) that are not burnable by a regular DVD burner.
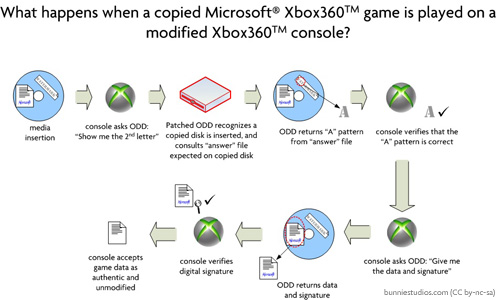
What the ODD modification does is redirect these requests to verify the watermark to an “answer table” contained in what amounts to a few files on the copied disk:
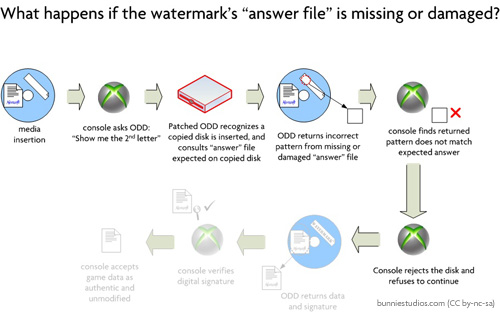
The most important fact to be cognizant of in this system is that the “answer table” is not contained anywhere within the Xbox360 ODD mod applied by Mr. Crippen. Without the user of the modification also contributing the “answer table”, the mod is entirely incapable of performing any function. This is demonstrated by what happens if, for example, the “answer table” is missing or damaged:
In the case that the “answer table” is lacking from the disk inserted into the ODD, the disk will not play. Thus, the question is: given that the user of the modified Xbox360 (in this case, the private investigators and agents that the government hired) must also materially participate in the “process” by providing an “answer table”, is the mod alone sufficient to justify felonious conduct?
Unfortunately, the answer is: “we don’t know”. Since the case was dismissed, the answer to this question is a cliffhanger; and the prosecution, now educated, should have a clearer roadmap for future actions under the criminal provision of the DMCA; I wouldn’t count on them making the same mistakes twice. Technical facts, such as the ones outlined in this post, and disclosed to the prosecution, don’t change from case to case … but the individuals, specific evidence, and overall angle of the case can change.

Hey… interesting read, a good primer to how Xbox360 protection works. Thanks!
Thanks for the article. Very interesting look at IP and DMCA. Do you think this will precipitate a change in how console manufacturers protect game data? Would it be safer for them to encrypt the data alongside the watermark and signature?
If they ever gonna encrypt game data with the water mark then the drive they use now will need to change. And the next step to the drive they are using are just what everyone wish for”Blueray”.
Bye-Bye SONY!!!!!!!!!!!
Interesting. Now does this mean that because the xbox odd mod does not decrypt data on copied games or even original games that it would not be a dmca violation. Also not if some one was to mod an xbox odd and to test it put in a linux distro, will that create any violation. I am very happy for Matt, but this still throws modding back to hide in the shaded area of technology and its legalities
we can’t fully say whether the mod would be a DMCA violation or not, since the case didn’t end with a decisive ruling
Personally I still think it does violate the DMCA, because its still a key step (you can put a burned disc with a proper answer file into a non-modded drive and it wont play) so the mod still facilitates the circumvention of copy protection, which based on my reading of the DMCA is still illegal
Hi Bunnie,
Quote: “As you can see, the ODD is responsible for returning measurements of watermark features (such as reflectivity) that are not burnable by a regular DVD burner. ”
Actually, that assumption is wrong. The DTR PDR (google is your friend) has been able to replicate X360 discs for several years, perfectly.
It is not to difficult to adjust recording density and manipulate ECC information with the right hardware.
:)
@RPS,
Umm, are you aware of who bunnie is?
The quote specifically states that these features are not burnable by a regular DVD burner.
The infamous product you are referring to, even if it isn’t vaporware, hardly qualifies as a ‘regular DVD burner’.
@Flagg
I am “aware” of who Andrew is. more than you are. The PDR is not vapor ware and is used to burn CSS content for MOD in a number of environments.
The reason I posted is that Andrew is patent unaware of the progress that has occured since his early days XBOX 1 hacking.
:)
Not really what you think. The thing is not available to regular consumers (and if it were, the Australian manufacturers would be in jail).
Moreover:
“Optical Content Protection (OCP):
DTR Ltd. has also developed a system to provide an anti-piracy solution to the copying of movie content on the DVD format … completely transparent to legitimate users … yet it does not allow for 1:1 digital replicas of protected content to be made onto recordable DVD media. ”
In short only legitimate manufacturers are permitted to buy and operate them.
More generally, even if you find a reseller willing to brave the DMCA penalties, it is technically illegal for you to use a bit-for-bit copier of any description to circumvent a technological prevention measure. That is why you cannot lawfully obtain a duplicator which actually does a bit-for-bit copy.
To take just two examples, Copystars DVD duplicators sell with a warning: they will not copy a protected movie, music, or game DVD. Similarly, since at least 2005 Primera duplicators carry a message like this in the manual:
“… DVD Duplication Limitations: For a DVD Duplicator, it will not copy any DVD that has Copy Protection encoded inside. Typically, most DVDs you purchase or rent from a store, does [sic] contain Copy Protection”.
Costwise, if you examine real disk duplicators available today you find they don’t do what you might think, and at $200-$600 a typical ‘duplicator’ isn’t cheap.
You might be able to pay a suitable firmware expert to sidestep the DMCA preventions, but real counterfeiters of course use glass-master techniques which are vastly more expensive. Base yourself somewhere like Antigua or Thailand or China, too, where the long arm of the WTO won’t get you.
Terry:
I quote: “Not really what you think. The thing is not available to regular consumers (and if it were, the Australian manufacturers would be in jail).”
Um, no, more like you didn’t read what I wrote. Firstly, you have quoted something that isn’t even related, as the “OCP” product on their site is not the same as the “PDR”.
As to the PDR, I have seen the device demonstrated in person (albeit, it was over 2 years ago now) and it was capable of doing exactly what is claimed. It can write just about any kind of protection to a recordable disc.
Your other quote:
“More generally, even if you find a reseller willing to brave the DMCA penalties, it is technically illegal for you to use a bit-for-bit copier of any description to circumvent a technological prevention measure. That is why you cannot lawfully obtain a duplicator which actually does a bit-for-bit copy.”
Pray tell, where does it state in the DMCA that it is illegal to create a “bit-for-bit” copy? One does not *circumvent* a TPM when one is *reproducing* the copy protection intact. They are not even close to being the same thing.
The modification/hacking of a system in order to *bypass* a TPM is what the DMCA is desgined to protect – but I think a valid legal argument in this case is that they are actually *putting the protection onto the disc* – and that in itself is not *circumvention* by any legal definition I know of.
Anyway, I have seen a vast amount of replication toys like the ones your mention over the years – and it is wrong to assume that the PDR also falls into that category. The system I worked on was using them to produce CSS protected DVD-Video on off-the-shelf recordable media – and with some prompting (on my part) they demonstrated the replication of several different types of protected DVDs, as well. Not magic, just decent engineering.
As to the legality, seeing as the they also use variations of the same tool to create copy protection, by extension would you also then imply that the DMCA makes it illegal to produce a system capable of developing the very same TPM’s required – in order to have circumvention in the first place? ;)
You seem to thing that creating a perfect copy is not circumvention of an effective copy-protection mechanism.
You are mistaken, as a cursory examination of case law shows. US case law disagrees with you. There are defences, (fair use in the US, fair dealing in Westminster jurisdictions) but making a “perfect copy” is still circumvention. That is, ‘putting the protection onto the disc’ is still a circumvention of a copy-protection measure.
All that making a “perfect” copy to ordinary media will do is add counterfeiting to a DMCA violation. Such a copy is in any event not perfect, as a recordable medium is not identical to a glass-master pressing. It may be functionally equivalent, but that is not a perfect copy.
Comparing the act of copying to producing a copier is a red herring. The product may not illegal per se but often it is in some jurisdictions. The latest case in the US dealing with that is RealNetworks v DVD-CCA (“… a federal law … [makes it] illegal to manufacture or traffic in a device or tool that permits a consumer to make such copies.”).
Outside the US the law can be a bit problematic. The DMCA is a US law not applicable outside its borders. But it is the US implementation of the TRIPS accords and WIPO treaty governing digital reproduction, so there will be an equivalent in in most countries’ “municipal” laws. They all outlaw the use of such a thing to produce the “perfect” (hah) copies you describe.
Some nations do permit a backup copy (the so-called “private copy” exemption). In my own country (New Zealand) for example, s81(A)(1) of the 2008 amendment to the 1994 Copyright Act permits it for audio. But you’re only allowed to make ONE such.
By the way: I quoted from the OCP manual because the PDR doesn’t actually exist as a defined product – you can buy something from DTR for a specific task but each PDR will vary. Even DTR’s own website observes that it is still a product “under development”.
It’s wrong to say that replicating a disk perfectly is not a violation. It has been held repeatedly, in multiple jurisdictions, that
Well well well, isn’t that something!
I just tried to use Google (and also for a laugh, Bing) and both of them no longer seem to return anything for the search term I posted above… ;)
In the spirit of free information, I’ll post the direct link here: http://dtrltd.com/products_pdr.html
:)
In the diagram “How are Micosoft game disks and DVD movies different?” you state that you can read computer code from the disc in cleartext. This is not the case however as all “computer code” is stored in encrypted form inside the xex file format. So this is actually a similiarity with DVD movies rather than a difference.
Nice clearly written article though :)
If anyone would know about this, you would — so just for my clarification/edification, is it true that the XEX format does not *require* the code to be encrypted? For example, I have seen (rare) examples of what seem to be unencrypted XEX files. Also, the King Kong shader hack was feasible, I believe, only because the shader code is not only unencrypted, it’s unsigned. Shaders are as much code as anything else … for the record, the specific PPC mnemonics included in the slide were provided only after feedback that the original block of hex code I inserted looked too similar to the block of ciphertext hex I inserted to represent an encrypted movie. A big challenge of preparing this was drawing a clear pictorial distinction between the two blocks of binary data, so I used exemplary machine language mnemonics to highlight the fact that binary code has direct meaning to some machines.
Regardless, the encryption of the XEX has nothing to do with the ODD modification, as the ciphertext is just passed through by the drive…thus explaining its details would probably only confuse the jury; instead, details unrelated to Mr. Crippen’s conduct are handled under the catch-all of “…and other data”. While I personally love going into the details, I had to exercise some discipline around keeping things simple and relevant.
I realise the xex has no bearing on the ODD modification, I was just pointing out that the diagram was using the cleartext computer code as an example of a difference between Xbox360 discs and dvd movies, when it is acually a similarity.
Yes xex files *can* be unencrypted, and while there are a few floating around, they didn’t come from game discs. I assume MS has strict controls in place to ensure the contents of a game disc doesnt contain any unencrypted xex files. Xex files are always signed however, just using different keys for development.
You are right that shader code is both unencrypted and unsigned, so that does count as “computer code” :)
One thing that got me was that Crippen was trying to use “homebrew” as a defense, yet the signatures employed do not allow homebrew. They actually enforce that *only* copied games will work. Using the “KingKong exploit” did allow for homebrew potential via a modified ODD, but that was long since closed by MS in console updates.
Thanks :-)
i am currently being sued by Sony for retailing the PS3key Jailbreak dongle. I am looking for an expert witness to argue with Sony’s claims. Bunnie, can I list you as a witness?
Thanks Bunnie, great story. I am kinda sad the case ended so quickly because i think it would have been very interesting had it continued longer. Still for Crippen’s sake i am glad it is over.
CGC Repairs: The rational answer is “no, the act of creating and using this specific firmware is not a violation of the DMCA”. The use of it however, is a different matter (and not within the scope of the case). And as defaultdotxbe implies, the DMCA, like many laws, may be interpreted within a range of possible meanings.
RPS: While I haven’t heard of that drive before, I find the info provided on the website http://www.dtrltd.com/products_pdr.html to be hilariously targeted to a specific audience…how have *they* not received a DMCA letter yet?
xorloser: Still doesn’t matter for the case at hand, which is probably one of the reasons it was dismissed :p
“creating and using” with respect to use with official media, of course :)
Shuffle:
I belive because that is because they do not sell these drives to the public, they are only intended for use in professional MOD replicator environments. In one of the early discussions with them I raised that very issue, their answer was “We are effectively providing a mini-mastering station, so we can are treated the same way as a pressing-plant (license-wise)”.
To me it’s evident that their goal is not piracy – infact, a little research yields that they’re actually behind a number of the anti-piracy optial disc signatures. So I think it’s more a case of they have a very cool tool that allows MOD to put protection onto discs to bring the downloaded content to a 1:1 parity with pressed media (same protection, tie app or game back to the disc, not to a single PC as with most download services).
I just found it interesting that the so called “impossible to replicate on recordable disc” protections – actually aren’t. For the record, I examined one of their drives back in 2008 for a MOD project and in discussions they told me that the PDR stemmed from their in-house development systems – that they used for R&D and to develop the very signature systems used to protect optical discs. :)
[…] USA v. Crippen — A Retrospective […]
[…] Huang was supposed to testify as expert witness. Today “Bunnie” posted some key concepts on his blog of what he was gonna present in the case:[QUOTE]While the true facts are not as simple, […]
THANKS. very interesting and wel written article
This argument hinges on the DMCA’s term “access” having a narrow interpretation/definition of just being able to read data off the disc.
It seems likely to me that in the context of console hardware modification that the term would cover the ability to play unauthorized copies of games on perhaps the only device that can.
The definition of the term “access” is murky, for sure.
However, consider the following scenarios that may help shed some light on the difference between “access” and “execution”:
Putting a book in a locked safe is different from a book written in arabic. In both cases, I can’t derive any meaning from the book, but in one case I can still flip the pages open and access the raw arabic text, even though it’s meaningless to me. Furthermore, the rarity of a language shouldn’t have a bearing on the legality of reading a text; otherwise, the Rosetta stone would be a tool of access circumvention.
Or, put in another perspective, conflating access control with ability to execute would imply that it’s potentially a crime to inspect the contents of exclusively-Mac software on a PC, and vice versa.
Also consider that construing a watermark to be tantamount to an access control would mean that I can now make it a crime for you to read printed material that has been watermarked with “unless your name is bunnie and this watermark is present, you are not allowed to read this page”; I could argue that your action of photocopying that page and thus removing the watermark constitutes the circumvention of a technological measure designed to control access to the printed page.
There are a lot of difficult subtleties to pick through when defining access controls; an overly broad reading of access control could result in a lot of splash-damage, while an overly-narrow reading could rob copyright holders of their ability to enforce their rights. But this is why things go to trial — to hopefully shed some light on these vague and ambiguous terms.
Essentially you’re right about ‘access’. Where the issue has surfaced in a DMCA context, like the Lexmark printer cases, the DMCA was ruled out because there was no circumvention prevention to stop the cartridge refurbishers accessing the firmware.
I’m just trying to say that it’s going to strongly depend on context.
The primary point of DVD’s CSS is/was to stop you from being able to read the contents of the disc.
The point of the 360’s access control is to limit you from playing unauthorized games/copies on the console, not to limit you from being able to read the contents of the disc.
[…] Huang was supposed to testify as expert witness. Today “Bunnie” posted some key concepts on his blog of what he was gonna present in the case:[QUOTE]While the true facts are not as simple, […]
[…] USA v. Crippen — A Retrospective […]
[…] for the purpose of encouraging discussion, criticism, and education, here are some of the key concepts I was to present in the […]
Being the only techie from a family of attorneys, I’ve finally got something REALLY INTERESTING to discuss with my parents! Great read! Thanks Bunnie!
The only good thing in this whole history, is that the modder was released.
I find this DMCA crap an absurd. If i buy and equipment, I want to be able to do whatever I want with it.. Much like the original xbox.. Nowdays I don’t even play games in it, But i use it all the time as a media center. Too bad I couldn’t jtag my consoles…
It’s not because of piracy.. it’s about freedom to do whatever you want with your stuff… Good thing laws such as this DMCA are probablt never gonna happen in my country, plus, new legislation is in fact prohibting anti-copy mechanims in some cases, as we are allowed to copy content from a CD to our Mp3 player..
The line of thought is, we buy the content, not the medium… so we have the right to listen ou watch it in whatever piece of equipement we have.. Now try passing a law like that in the US.. You’ll probably wake up dead the next day after you propouse something like that.
In fact, I think corporations are running that country a since a long time ago..
Wake up dead… smart
Which is why it is important that you go out and buy a whole lot of Bunnie’s Chumpies, and similar hack-o-friendly devices and do some great stuff with them instead of buying closed devices such as XBOX’es, PS3’s, Wii’s etc.
And the creativity among hackers is enormous. Just look at what has already been done with the Kinect – even without official drivers.
[…] Andrew “bunnie” Huang’s blog […]
[…] “bunny” Huang, a proposed defense witness and inventor of the Chumby, has posted a blog entry outlining his proposed testimony in US v Crippen. Mr. Huang explains the Xbox360′s […]
ok im sorry but you totaly lost me and i have been moding my consoles since snes and the gamedoctor from bung,you totaly lost me at the awnser table not beng flashed to the drive ,so what you are still copyint the awnser table right or are you creating it?my point is there is no way in holy hell that anyone can find 12 people in this country that are going be able to under stand a word of this shit no matter how simple you think you may have explained it,and then on top of that they would need to be able to all the legal jargon in th dmca law itself too,you would need 12 jurors with phds’ from both harvard law and mit and i bet they would stilll have trouble
you want to make you case to a jury just go with the “i never even heard of dmce legislation defense”go out on the street with a vid camera and start asking everyone you walk by if they ever hear of dmca laws ,i gaurentee you not a 1 will know ,if the judge objects then start asking the jurors,this is all crap legislation passed by greedy big busniess, lobbying and special interest anyway
anyone remember the old obsolete divx players that came out when the first dvd players came out you could buy a disc but after you watched it like 5 times it locked you from viewing it again ,i think you could call up and purchase a code that let you access it again for how ever many more views ,anyone know how that type of encryption worked
[…] Source […]
i hpe this crippen dude is going to sue and press criminal charges against microsoft and this private investigator for secretly recording him,this is totaly illegal,i would sue the the p.i for this and press criminal charges against him and his company/firm if it exists,i would also press criminal charges and civil suit agaist microsoft for encouraging this guy to secetly record him,and also for wrongful proseccution he should be able to get money back for legal and court fees as well as sue for emotional distress
and lost wages ,not like he has anything to loose they cant do anything to him on account of double jeopardy.also isnt funny that this case was kept out of the mainstream media you think you would have heard something about this on network news,could it be that m$ realize their douce bags and that this is really not the best move for them in terms of P.R.
I just ordered the 8 inch one for $67.99 at Best Buy and the 3.5 inch one for $39.99, each with free shipping…
These prices didn’t come up by going directly to the Best Buy site (those produced the $99.99 and $49.99 sale prices), but instead by searching via Google Shopping for the small one at $49.99, but the link leads to a $39.99 price. Strange.
>In some respects, it’s a setup for prosecutors to prepare
>a stronger, more informed case in the future.
That was the unsatisfying aspect of it for me, he got off on a technicality of California-specific law, and nothing more, so it doesn’t appear to be much of a landmark DMCA case at all.
Just for your information, in the USA, when a case is dismissed without being tried and a jury verdict returned, the “DOUBLE JEOPARDY” statement does not apply.
The prosecutor may well be smarter then you seem to want to give him credit for. Perhaps he realized that he was on shaky new ground fraught with problems and decided to not risk creating an adverse action at that time.
It is far smarter for the DA to dismiss very early if he realizes his case is too weak. SO, the defendant is able to be retried subject to any statute of limitations that may apply. There is no “double Jeopardy” application in this case.
SORRY !
Nice, neat work! Happy I came by your post first to have read this!
[…] here for his blog post on how the Xbox security mechanism works. You can order the book, “Hacking […]
Just like the put up, it’s preferrred to concede somebody seeing impatient about one’s voice apart from prepare owing to I am!
Hiya, I’m really glad I have found this information. Nowadays bloggers publish just about gossips and net and this is really frustrating. A good blog with interesting content, this is what I need. Thanks for keeping this web site, I will be visiting it. Do you do newsletters? Cant find it.