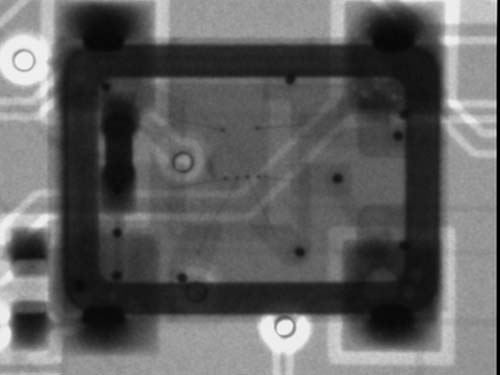
The Ware for July 2007 was indeed a pair of crystal devices. The top image is an SMT crystal oscillator. It embeds both a quartz crystal and some active circuitry to create an autonomous CMOS-level frequency reference. The bottom image is of a “tuning fork” quartz crystal–you can see the mounting for the tuning fork structure in the X-ray–and it is a passive device that requires an external chip to cause it to oscillate.
The bottom device is actually a sort of “trick question”. Nobody got it exactly right! The interesting thing about the bottom image is what it looks like in visible light:

Compare it to the X-ray:
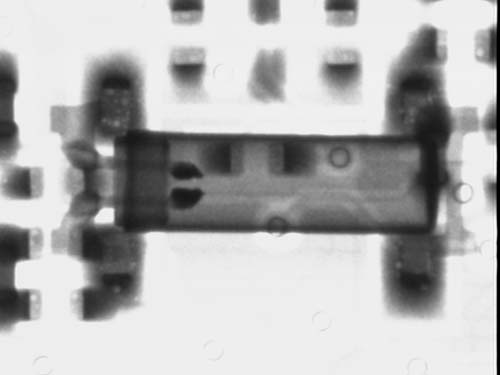
You may ask, what is going on? Well, the X-ray goes right through the plastic, so you don’t see it in the lower image. Instead, you see the shadows of a classic “metal can” oscillator. Why would someone go through the trouble of burying a metal can in a rectangular plastic case? The reason the overmolding is done is to allow the part to be machine-assembleable. The round can normally used for these watch crystal oscillators are difficult for machines to pick up and place, whereas a flat plastic surface with four pads is much more amenable to the vacuum tweezers used for automated assembly.
Participants in the contest could have called it out as an overmolded device because you can see the dark shadows of the four pads used to tack the device to the board in the x-ray…well, at least none of us are radiologists trying to diagnose a patient, thankfully!
The winner for Name that Ware July 2007 is Hugo! Congrats, email me for your prize. This one was relatively easy to judge, thankfully. I’m of course behind on getting August’s up (my, it’s September already!) but I wanted to spend some time on the Made in China series before catching up on Name that Ware.