Well, it’s been a long June. Actually, it’s been a very interesting past couple of months; some of the most interesting stuff will appear on this blog in late August, but for now I have to keep quiet about some of the things that have been keeping me busy. I’ll drop one hint, though–I’m working on a project that has an open source hardware aspect, and I am looking forward to sharing the details with everyone once things are rolling. I’ve always felt that hardware should ship with schematics and source code, and I finally have a chance to make good on this notion. I also did a bit of the conference circuit this past month, with a talk at Recon 2006 in Montreal and the National Youth Leadership Forum on Technology in San Jose.
I apologize for missing June’s name that ware; to make up for it, the next name that ware contest will have two wares. I actually had a ware all queued up and ready to go, but the combination of an exciting July 4th holiday and tons of travel for the past couple of weeks, as well as a deluge of spam on the blog, has kept me away from posting. If anyone posted a comment in the past month, there’s a very good chance I accidentally marked it as spam, because as I mention in the previous post I was getting upwards of 50 spam posts a day. The upgraded blog software and spam filter seems to have fixed this problem, thankfully.
For May, 2006, we have a number of winners! I’m glad that so many people participated in the contest. jimmyjo, roastbeef, and christian all win prizes this month (email me to pick your prize and I’ll send it on to you!). jimmyjo and roastbeef both got an easy and medium ware correctly. Christian went all the way and jumped headlong into one of the hard ones!
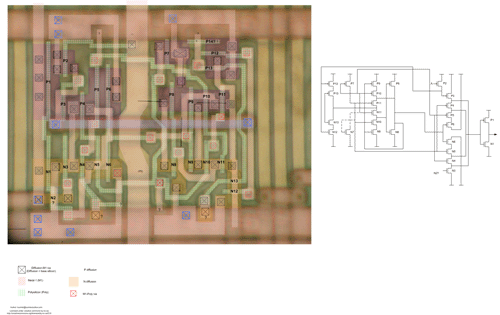
Honestly, when I selected the hard wares, I had no idea if I could figure out what they were, or if they were even do-able, but I wanted to put something up that wasn’t as simple as an inverter. It turns out that they are indeed quite difficult to decipher, partially because M2 blocks some key devices, and partially because the area photographed is not large enough.
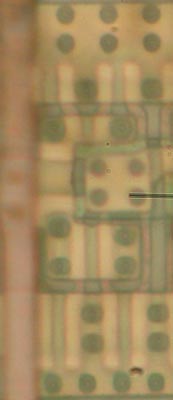
While I am not 100% sure of any of my own solutions, I can talk y’all through what I think they are and why. Hard(3) is most likely a simple D-latch or flip flop. The cluster of transistors on the right side, underneath the crosshairs, form a pair of cross-coupled inverters. The cross-coupled inverter motif is the core of any static memory cell, such as those used in a flip flop. Hard(2) turns out to be un-doable, I think, because there is too much M2 running over it: there is a large inverter to the left of the crosshair, and then the logic gets a little more exciting to the right but I gave up.
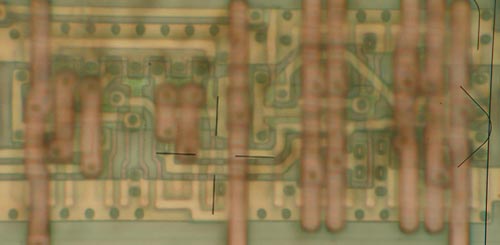
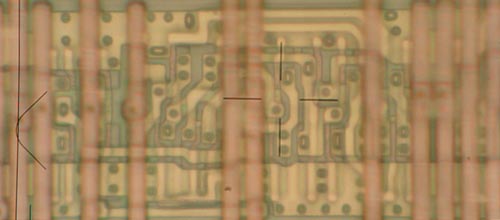
Hard(1) I spent some more time on, because Christian did so much analysis I had to do my homework too to match his efforts. Click the image below.
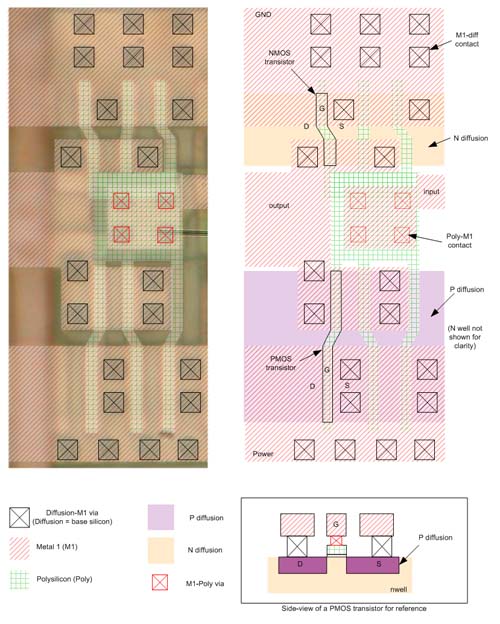
There are approximately 15 p-type and 15 n-type transistors in this CMOS circuit. As you can see, there is some action happening underneath the M2 power straps that obscures the total function of this cell–I have interpolated some devices and connectivity through symmetry arguments. Also, the huge strap of M1 going through the middle of the cell seems indicative of some kind of clock or strobe-type of signal. The partial schematic on the right helps reveal some of the internal structure. P8-P11 and N8-N11 form some type of cross-coupled inverter pair. If the chain of P9-P11 and the chain of N9-N11 are all activated at once, you can see that (P9-P11/N9-N11) and P8/N8 form a cross-coupled inverter structure. When I first started decoding the circuit, I thought for sure this would be a sense amplifier, but there are some fancy things going on, that look related to controlling set/reset possibly, or perhaps rolling in some additional logic to the storage process as an optimization. If I were to guess as to what this is, it’s some type of flip-flop, I think, but with some extra logic rolled into it for fancy set/reset, muxing or J/K style controls. I suppose if I poked at this some more I could figure out more, but I want to post this and get next month’s wares up! :-)