The Ware for February 2019 is the old circuit breaker on my flat. It’s a classic, perhaps from the 70’s or earlier; the outer case is so weather-beaten, none of the markings are legible except for the rated capacity (40A). The breaker had been getting progressively more fussy, tripping at random times of the day, so it was time for it to go and get replaced with a new one. It’s definitely annoying to have your power go out at random intervals once every couple weeks. Since it was going into the bin, I figured I’d take it apart and see what I could learn from it. Gratz to phantom deadline for guessing it very quickly (again), email me if you’d like to collect another prize!
Winner, Name that Ware February 2019
March 30th, 2019Supply Chain Security Talk
February 27th, 2019I recently gave an invited talk about supply chain security at BlueHat IL 2019. I was a bit surprised at the level of interest it received, so I thought I’d share it here for people who might have missed it.
In the talk, I relay some of my personal trials authenticating my supply chains, then I go into the why of the supply chain attacks to establish some scenarios for evaluating different approaches. The talk attempts to broadly categorize the space of possible attacks, ranging from attacks that cost a penny and a few seconds to pull off to hundreds of thousands of dollars and months. Finally, I try to outline the depth of the supply chain attack surface, highlighting the overall TOCTOU (time of check, time of use) problem that is the supply chain.
The main insight is that transparency or openness of design by itself does little to secure a supply chain, because the entire situation is one huge TOCTOU problem. Checking hardware design files, locking down the assembly line, and Fedexing the product to your office is like hashing and signing your source code, running it through a trusted compiler, and then sending the binary unencrypted over the Internet and trusting it because it was “thoroughly checked”.
The inverse analysis is equally daunting: in software, one may copy each binary into RAM, hash and check its cryptographic signature, and run it only if it checks out. For hardware, there is no equivalent of “hash this instance of hardware and check its cryptographic signature” before use: “hashing” hardware involves taking it apart and inspecting every transistor and wire, which is both impractical and likely to render the hardware non-functional.
Thus while open source hardware does engender some benefits for security (such as disclosing μ-state for Spectre side-channel analysis and ensuring no backdoors due to design oversight), it addresses a separate problem domain from supply chain attacks. While an open source hardware phone is arguably more trustable than a closed source one, open source is necessary but not sufficient for it to be trusted.
I do have some ideas on the practical mitigation of supply chain attacks, but they are still a bit too green to blog about. Stay tuned…
Name that Ware February 2019
February 27th, 2019The ware for this month is shown below:
One of the ideas of name that ware is to learn by taking apart everyday objects. This one came across my desk under unfortunate circumstances, which lead to me dissecting it and snapping a couple photos to share!
Also, in the pantheon of wires I have known, the wire below holds a special place: it was literally part of me for several months. In fact, if you look very closely, you can still see bits of me attached to the wire.
Most interesting is how my body built a custom cable chase for the wire as the bones healed:

Now if I can only get my robots to learn this trick, it’d save me a lot on zip ties…
Winner, Name that Ware January 2019
February 27th, 2019The winner for January 2019 is Adam! Congrats, email me to claim your prize. This ware was an easy one, but I love retro-wares like this TI PHP1500 speech synthesizer. One of my first real hardware projects was building a SPO-256 based speech synthesizer card for my Apple II back in high school, so this one is particularly nostalgic for me.
Thanks again to Jesse for contributing this ware!
Name that Ware January 2019
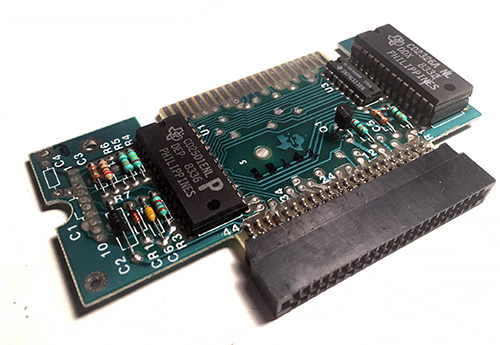
January 31st, 2019The Ware for January 2019 is shown below.
Thanks to Jesse for contributing this handsome retro-ware.
This one should be a cakewalk — I did not blur out the part numbers because I felt like by the time I finished obscuring the ware there wouldn’t be much left for guessing! Instead, I’m just appreciating a retro-ware for what it is — a reminder of a time when not everything could be done in software, and we had to rely on special purpose chips to do even the simplest of things.
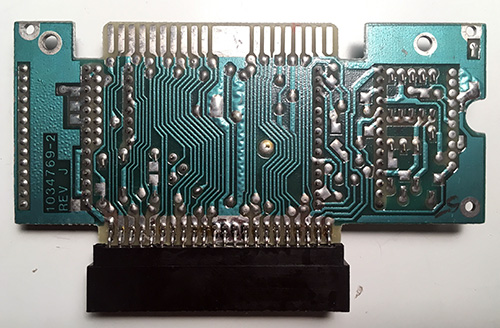
I also included a picture of the back side of the board because it illustrates a common problem seen in PCBs from the 80’s — namely, what happens when soldermask is applied directly over tin/lead plating. Tin/lead can be used as an etching barrier; conveniently, once the etch is done, the tin/lead plating doubles as the solderable finish for the PCB. So, if you scrape back the soldermask of the older PCBs like this, you won’t immediately find bare copper: you’ll first encounter a layer of tin/lead plating.
Unfortunately, when the PCB is subject to reflow temperatures (and particularly wave soldering), the entire tin/lead layer liquifies, and excess solder from the pads will flow under the soldermask, creating the wrinkling, ripples and bumps seen under the larger traces.
Modern PCBs still use a tin mask as an etch barrier, but the tin is stripped off entirely before the soldermask is applied (hence the term “SMOBC”, or soldermask on bare copper), and then solder is re-applied to all the pads using a HASL (hot air solder leveling) process (or ENIG, OSP, or whatever finish is required). Seems like a lot of work to apply a finish only to strip it off, but bare copper won’t allow solder to seep underneath the soldermask, so it’s worth it.