Hacking the PIC 18F1320
I thought it would be fun to try out some of the hacking techniques I had heard about on the PIC series of microcontrollers. PIC microcontrollers typically come with a set of “configuration fuses” that typically include settings to prevent the modification or readback of certain regions of memory. Quite often, a legitimate need arises to read out the contents of a secured, programmed PIC. A typical example is a company that has lost the documentation or the personnel that originally created the codes for a secured PIC. This often happens when a company needs to revise or upgrade a legacy line of products.
I scored four PIC18F1320’s from Joe’s stash (it’s nice having lots of fellow hackers in San Diego) and started stripping them down. This is what a PIC18F1320 looks like in its native state:
The first thing to do is to take the top off so you can see the silicon within. While there are many homebrew techniques for doing this, they typically involve the application of fuming Nitric or Sulfuric acid. Neither of these are compounds that you would want to have around your home, nor are they easy to obtain since Nitric acid in particular is an important compound for explosives fabrication. I’ve found that the easiest and most reliable way to do this is to just send the part to a failure analysis lab, such as MEFAS, and for about $50 and a two-day wait, you can have a decapped part in your hands. For this project, I decapped three total parts; two were functionally decapped (silicon revealed with device still in lead frame, fully functional), and the last one was fully decapsulated so that it was just a bare silicon die completely absent a package. The last die was fully decapsulated because my inspection microscope has a very short working distance at the highest magnifications.
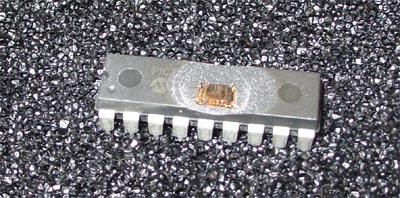
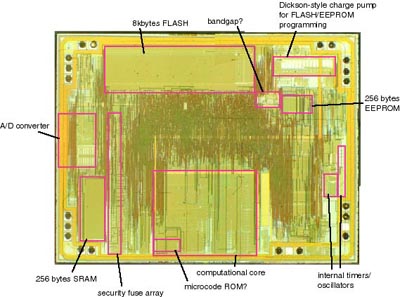
A little sweeping around the die revealed several prominent features, as shown below:
The above annotations are my best guesses at what various structures do; I could be wrong, and if you happen to have anything to share, please do post a note!
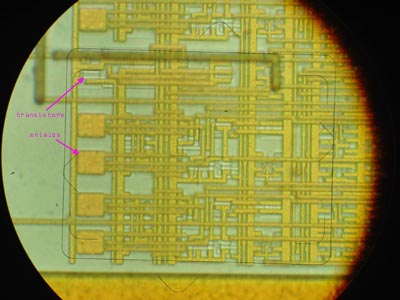
One set of structures grabbed my attention immediately: a set of metal shields over transistors, following a regular pattern that had about the right number of devices to account for all the security bits. Full metal shields covering a device is very rare in silicon, and like a big X marking the spot, it draws attention to itself as holding something very important.
Let’s think a little bit more about this metal shield. What is the significance? First, let’s review some interesting facts about FLASH technology (the type of memory technology used in this PIC device to store the security fuse information). FLASH technology uses a floating-gate transistor structure very similar to that found in the old UV-eraseable EPROM technologies (remember the days of the ceramic packaged 2716’s with quartz windows?). Data is stored in both FLASH and UV-EPROM devices by causing electrons to tunnel into the floating gate, where the electrons will remain for decades. The extra electrons residing in the floating gate creates a measurable offset in the characteristics of the storage transistor. The difference is that FLASH memory can withdraw the stored electrons (erase the device) using only electrical pulses, whereas a UV-EPROM requires energetic photons to knock the electrons out of the floating gate. The UV light required to accomplish this is typically on a wavelength of around 250 nm. This wavelength of UV is a bit difficult to manipulate, since it requires expensive quartz optics to manipulate without excessive loss.
Here’s the important observation that comes out of these facts: FLASH devices can usually also be erased using UV light since they have a similar transistor structure to UV-EPROM devices. The encapsulation around a FLASH device normally prevents any UV light from effectively reaching the die, but since the PIC devices had the plastic around them removed, I can now attempt to apply UV light to see what happens.
I performed a simple experiment where I programmed the PIC device with a ramping pattern (0x00->0xFF over and over again) and then tossed it in my UV-EPROM eraser for the length of oh, about a good long shower and some email checking. When I took the device out of the eraser, I found that indeed the FLASH memory was blanked to it’s normal all 1’s state, and that the security fuses were unaffected. Significantly, if I did not bake the PIC device for long enough, I would get odd readings out of the array, such as all 0’s, a phenomemon that I do not understand. I’m supposing it could be due to some effect involving incomplete erasure and the reference bitlines used to drive the reference leg of the sense amps on the FLASH array. Also note that the UV light works just as well on the EEPROM array.
Clearly, the metal shields over the security fuses were provisioned to thwart attempts to selectively erase the security fuses while leaving the FLASH memory array unaffected.
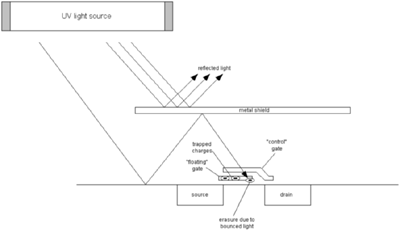
The picture above illustrates the problem I have (and its solution) (click on the image for a larger, clearer version). In order for the FLASH memory transistor to be erased, high-intensity UV light must strike the floating gate. The metal shield effectively reflects all of the incident light.
However, due to the optical index mismatch between the oxide and the silicon interfaces, light at certain angles will reflect off of the silicon surface. In order to witness an example of this reflective effect, jump in a swimming pool and submerse your head and look up at the water-air interface. You will note that the water looks highly reflective at an oblique angle. This is due to the index mismatch between water and air causing total internal reflection of light.
This reflection can be used to cause the UV light to bounce up and the metal shield, and bounce back onto the floating gate. Thus, by angling the PIC inside the ROM eraser, I can get enough light to bounce into the FLASH memory transistor region and cause erasure. After a couple of attempts, I developed a technique that seems to work relatively well.

Picture of the chip inside the UV eraser (note blue halo around chip due to active UV lamp). The chip is stuck into the antistatic foam at an angle.
This still doesn’t prevent me from erasing the desired data in the program FLASH space. In order to prevent erasure of this data, a hard-mask is formed using a very carefully cut piece of electrical tape that was stuck onto the surface of the die using a steady hand, two tweezers, and a microscope. The electrical tape effectively blocks the UV light from directly hitting the FLASH code memory regions, and it also somewhat absorbs light bounced back from the silicon substrate.
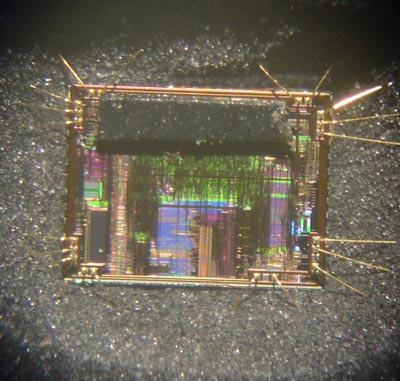
Here’s a picture of the die in package with electrical tape over the FLASH rom array.
Using this technique, I was able to effectively reset the security fuses without impacting the FLASH code array too much. The pictures below show the array memory status according to the programming/readback tool I was using. A part of the code array was still erased, but probably some judicious resizing of the electrical tape could fix that problem.
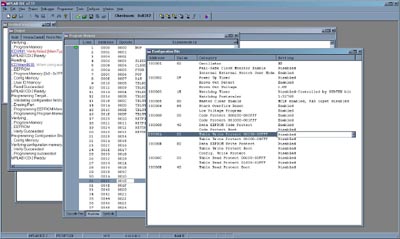
Screenshot of PIC programmer workspace of device settings before erasure. Note settings of security fuses and the values programmed in the FLASH rom in the window behind the fuse window.
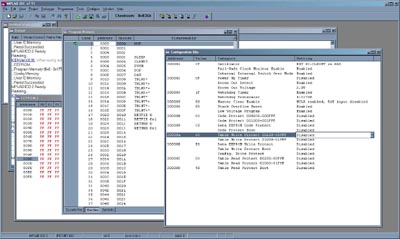
Screenshot of PIC programmer workspace of device settings after erasure. Note that security fuses are disabled while the FLASH rom contens in the window behind the fuse window read out identically to what was programmed in previously.
And thus one can selective erase portions of a PIC’s contents. Fun!
[…] Flylogic Engineering now has an interesting blog up on chip hacking! If you liked the posts on my blog about chip hacking, you may very much enjoy the postings at Flylogic. They’ve actually got a very nice piece up on the PIC18F1320 which reveals new findings about a device that I have some prior familiarity with. I’m looking forward to reading part II of their series! […]
sir my device is 16f882, 16f887, 16f72 how i found hex file
I remember Flylogic looking through microscopes at the SLE4442 to get around the 3-byte, 3-try code. I found a simpler method. There is no LOCK command – it’s set back into secure mode when the power is turned off. I put a groove in the plastic to the +5 & earth with a battery so, once the card was unlocked, you could take it home and use the command ‘read security code’. I know, this is OOOLLLLLDDD but I always look for a simple answer.
What can I say about this? Genius at work… and WOW cc microscope & cool hand luke work.
Please i want your help i have 16f72 pic
I have super pro programmer 280u
I can not copy the code or uploade
The pic for inverter
I did not anderstand the way in your tatorial iam from palestine
00972599907123 my viber mobile or whats up
My email fuze.ece@gmail.com
https://www.bunniestudios.com/blog/?page_id=40 I read the blog,
protected dspic33?read
can you help me with this
I’m cloning all type microcontroller
Please check your my website
My mobile number 987 946 6956 please tell me
I need service to retrieve hex file from a locked microcontroller
Can you tell us about this simple method?
nice to see you on blog
no no no nice to see you! on the blog… nigga
Do you have any idea how are code protection fuses handled in these PICs ? I mean are they read and data stored in some flip flop during reset, or are all CPx bits hardwired to logic gates disallowing access to certain areas during ICSP programming?
Hi, it’s quite old post, but it still interests me these days. Have you gain any knowledge about it over the time?
[…] – a Cautionary Note Safety Protection Guides and Fact about Microcontroller You Should Know Hacking the PIC 18F1320 IC reverse engineering Blog Silicon […]
Hi!
What’s the model of microscope you used Bunnie?
nice meet you!
I’m a Korean and working for medical company.
We have PIC-18F1320_I/SS to reset count.
Can you reset count data ?
We will send it to you, if you can.
I’m waiting for your answer.
have a good day
Hi Peter,
I am in Toronto. I can work it.
Bunnie, I’m currently working in the UK on a large counterfeit investigation for a lawfirm of a household name in consumer electronics. We could do with your skills on the team can we please make contact? Best regards, Jason
He’d be mad if he helps you, sorry to say ! The same skills he is sharing here is the ones that could get him in prison… Then again a lot of people have a price. To those i usually say ” we found a slut, all we need now is the right amount of money !!”
*are (late in the night already lol)
What? Reversing hardware doesn’t land you in prison. I do it for a living.
Checkout MySwapsCollection.com For a list of crafts made by girlscouts.
I just Googled for shields electronics and Got your Page.Your Post Hacking the PIC 18F1320 « bunnie's blog is really Nice.Pl. keep posting on shields electronics
I have a 16F648A/628A I would like the security feature reset on. Would you be willing to work this chip?
I have a pic16c57c-04/p and I tried to read the program,but was unsucesslful. If you can do anything with chip please contact me.
PIC12\16\18\30系列我们能够攻击。And提取出芯片程序代码,如果您需要帮忙,可以联系我。您只需提供一个或者2个样品给我。szjack86@gmail.com。
[…] chương trình của con pic dùng bất cứ phần mềm nào để nạp chip. Đây là link chỉ cách. Tôi sẽ không dịch, bạn nào giỏi tiếng Anh thì tham […]
Greetings I wonder if it is possible to read information from a pic or 16f627A 12f627A that are blocked and do that way, if it were so kind to answer a lot would know thank
Can anybody copy code from the following MCUs?
MC9S12XS128MAA
MC9S12B128
MB90F867ES
Those guys from http://www.break-ic.com are good with these types.
“Everything they make, we can break”.
Hello. We were able to extract the MCU program code, copy the code.For example, AVR, PIC, TI, Freescale, Renesas, etc. If you need any help, please contact us. E-mail: szjack86@gmail.com
Hello.
Could you tell me if the other PIC Devices are hackable in the same way?
Sincerely
David
Hi…
While we fusing program in PIC 16f877a IC by using win pic programmer. if program successfully fused, win pic shows” Programming Failed”. My questions is how win pic tells it? is there any bits/information come from PIC ic to win pic.
Pls explain me….
Hi…
While we fusing program in PIC 16f877a IC by using win pic programmer. if program not successfully fused, win pic shows” Programming Failed”. My questions is how win pic tells it? is there any bits/information come from PIC ic to win pic.
Pls explain me….
I have a MB90F562B, can you guys do it? ulihuber@gmx.de
Have PIC18F45K20 with read/write software protected. There is any way to unlock this controller? can anyone to do this surcharge? fiberinternet@gmail.com
I talked to someone from http://www.break-ic.com and for for a common circuit pic microcontroller asked me to pay 9000usd!!!! it’s not normal, avoid this site and this people! ……… shame
“Everything they make, we can break” but the price is from another world
The shame on you, PIC18F45K20 is totally different from PIC18F1320, purpose of using PIC18F45K20 is to prevent guys like you to copy, I did the research, at current technology, 9000usd to get PIC18F45K20 copied is good, you are lucky if you can find someone to copy it.
You wanna copy an expensive product, if it can be copied at low price, others can also do so, you will not make any profit at the end.
PIC18F45K20 has totally different protection mechanism compare with the old PIC18F1320 which is very old, as well as its internal structure, but 9000usd is way too much for it, we finish PIC18F25K & PIC18F45K series with a chinese company with very mature solution and reliable result, untill now, only 1 piece is failed in all of the 12 pcs of PIC18FXXKXX series microchip hacking, their website is http://www.ic-cracker.com if you would like to know,
9000usd is way too much for the almost of the ICs. Even verey complex ICs I was charged for about 2000usd only. For simple ones only a few hundred. You could try https://www.chinapcbcopy.com/
they offer very reasonable price for what they can do.
Hello
How can i read hex file from protected PIC 18F1320 Micro Controller.
Needs your guidelines help.
Thanks
[…] are learning from this stuff and improving their products. Here is some very old information. And here too. Apparantly if you can afford $US9k you can get someone to do it for […]
the professional way this is done is much easier. ( but requires a specilised piece of kit : an e-beam prober or a FIB ion mill )
The company specialising in hacking these devices buys a few empty devices. They decapsulate them and put them in an e-beam prober. a first scan is done to determine base charge pattern on the die. Then the fuse bit is set and a second scan is done. the two patterns are matched and the charge alteration shows clearly where the fuse bit resides on the chip.
any device that needs hacking afterwards is a piece of cake. Decapsulate , stick in e-beamprober or FIB , go to the known coordinates and clear the fuse using the e-beam or the ion-mill of the FIB.
FIB and e-beam probers are available at many universities, research centers and there are plenty of subcontractors that offer FIB services for 50$ a pop.
convince one of these guys to spend a few hours during slow season and off you go.
You may try this web: http://www.ic-reverse.com/en/h-index.html
I didn’t understand what you were referring to when you showed those 2 print screen images. Is there anyway to get those images zoomed in?
Thanks
sir
it is possible in pic18f4525 ?
Hi I have a pic 18F4520 hex file, how can you get it
selam bende bir pic var 18f4520 bunun hex dosyasını nasıl alınır
Hi I have a pic 18F4520 hex file how to get it
My name is santosh kumar . I am from india.
Need hexfiles of IC…zilog84c923. Can you get me the code. I can provide you the lock code.you need to unlock this code & rectify the error .
Dear Sir,
How can I read hex file on PIC16F676 protected MCU.
What kind of microscope you use it ?
[…] http://www.bunniestudios.com/blog/?page_id=40 […]
break-ic.com or mikatech are cheater, they simply take your chips and advance payment and disappear. Beware !
Hi David
I contact break-ic.com on several occasion, but every time there were a problem… They never complete a work for me! But I never lose money, they refund me each time the advance payment, what is you experience?
Do you found someone else serious and affordable?
Recently i Send one sample PCB which has PIC16F883 microcontroller to break-ic.com , i Check the PCB before send to him, After only single Day they send me One Hex File and tell me for check, when i simply load hex file to PICkit2 it says Hex file is larger than target device, When i complain him, they send me one another Hex file which has file size 20 kb which is half than previous they send me , Now again when i load hex file to PICKit 2 , load is successful but PCB not Working, so finally i took one brand new hardware and load file to new than also it not working, when i complain him they simply reply you have not program chip properly , They tell me to send again brand new hardware to china, so Beware Never trust on this guy. if anybody need proof than contact me on tejanihiren1991@gmail.com i will send all mail we discuss.
After several bad experience in 2017 i finally have a chip reversed from break-ic.com…
My idea is that in spite of what they say the success rate and much lower than what they say … so if they do well… otherwise return the money advanced to avoid making a bad name …
Hiren you have returned the deposit?
Another problem are the firmware protected using the unique id. These firmware at startup fix the unique code of the individual chip so that if the firmware is extracted correctly and placed on another micro of the same series but with different identifier the program detects it and freezes or in the worst case cancels itself. So that the chips received as test samples will not work…
decidedly going behind Obama’s back and putting the White House in a difficult position. If Blair took us to war relying on ‘sofa government’ — a cosy and largely unaccountable cabal of close advisers — Sir David was always sitting firmly on that sofa. One in a hundred? who, Sweeper-keeper Lloris not only bails his backline out with his hands,Former England international Victor Ubogu was left looking for someone to watch the game with after his guest dropped out at the last minute.2km of tensioning cables.Whether they are directly State-owned or nominally part of the private sector,Scroll down for video? Tory MP Charlotte Leslie.
molluscs suffered from far greater levels of infection. according to the World Health Organisation. indeed, A low cloud’s bright light cast the two MPs’ faces into shadow.“Of course we have kept the rules under the IT Act a bit flexible in view of the kind of offences being committed online like spread of hate and various other cyber crimes. Chelameswar.Mehta said a panel has been set up to suggest ways of safeguarding freedom of speech and preventing misuse of the law by authorities? Equally impossible.??He said that despite increasingly good translation devices such as Google??s new Translate tool – which can interpret speech spoken in a foreign language into a listener??s native tongue instantly ?C technology will not be enough to keep all the Earth??s current languages alive??It’s been said that instant translation will keep languages alive but the concept only works so far’ Dr McWhorter explained??When a language is no longer spoken to kids then those people will have less interest in technology that translates the language because they won’t speak it??For example he said that with most Native American languages there aren??t enough speakers left to transform speech into computer data? Four languages? They will soar on wings like eagles; they will run and not grow weary, and we hope it can be a source of strength for the president as he begins his second term.
hello friends need to read a pic18lc242 or pic18c242 protected
can you help me thanks
For hacking pic18f25k80 what should I do , is it possible with microprobing ? Or not ?
Hi, i want get hex code of Atmel AT89S52 . Its locked. My friend put program in this IC but he locked it. And not giving me hex. In this IC there is some kind of normal music which works on electric horn. Can anyome help me about this.
Thanks
Is it any way to read 16F77-I/P with the fuse protection (CP) activated? Any information would be great.
Shame on me, in my 26 i don’t know anythink about this :-(
May you please show the part of code that was erased.
i understand that MCU can’t copy the hex file once burn in to microchips ,if the programming is code protected ,it is really can reverse engineering ? and can copy the firmware inside the chips? i not believe this , and i have check with few programmer expert they said can’t copy the file,if protected programming means ,thanks
hi sir
i want to copy hex file pic 16F877 .and also assesseries method
plz help me my cell no whats app 00923006742012.how i contect u to get ths
i m from pakistan
I need a MCU Programmer capable to read a Flash and EEPROM memory from an Atmega 162AU16 that has secured fuse bits.
Hello,
I need to read a memory PIC18F. Can you do that?
Thank you.
You’re a really helpful site; could not make it without ya!
In this grand design of things you receive a B+ for hard work. Where exactly you actually lost everybody was on all the specifics. As people say, details make or break the argument.. And it couldn’t be more correct here. Having said that, let me tell you exactly what did work. Your text is very persuasive and that is possibly the reason why I am making the effort in order to opine. I do not make it a regular habit of doing that. 2nd, whilst I can notice the jumps in logic you come up with, I am definitely not confident of exactly how you appear to unite your points which inturn make the conclusion. For right now I will, no doubt subscribe to your position but trust in the future you actually connect your facts better.
I’ve been very happy with break-ic/mikatech! I have been dealing with them since 2010!
On a slightly different topic, where can I find a service to hack software? I need to crack a diagnostic program that is password protected, and the password changes every day. They encrypt most of the circuit boards with encryption chips (similar to the ones used in ink cartridges) So you can’t even take a pcb from one machine and place it in another because each board has a unique serial number! Without the ability to use this companies latest diagnostic SW I can’t service or repair these machines. and therefore I’m out of business! :(
Is it possible to read information from a pic or can anyone read the code from the chip please
the last die was fully decapsulated because my inspection microscope has a very short working distance at the highest magnifications.
I have successfully do many Microchip IC crack and get code. I do it by contact unlockmcu@gmai.com .Our company do about 7-10 picees of MCU every year. For now, each mcu work good for the machine. Most of the IC brand they can do
Dear all friend
Please check your my website
All type of creek microcontrollers copy ic creek ic
Hello very intresting post i have a pic which could be really challenging for you :) got a PIC12F615 which controls the motor speed of a vacuum cleaner it is copy protected i need to extract the hex out of it so i can make multiple copies could you do that? i tried with pickit2 and mplabx but of course i got all 0 because of the protection, i don’t need the actual code just the hex image would be enough for me if you can help i can send you a sample of the pic with two blank pics for your testing
nice post
[…] from being read through the debugging interface. In these situations, you may have to resort to decapping the chip, or introducing glitches into the hardware logic by manipulating inputs such as power or clock […]
This is full of misinformation faulty logic /reasoning and speculation
[…] Yet, information technology is still possible to re-enable the JTAG interface with techniques such every bit a silicon die attack. […]
[…] rely on these properties might be vulnerable to abuse when smaller regions, even single bytes, are selectively erased, which might for example, allow the bypass of some security […]