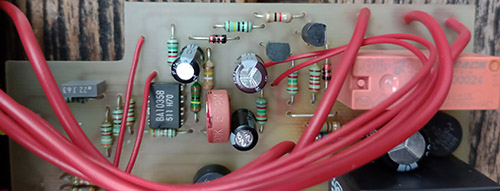
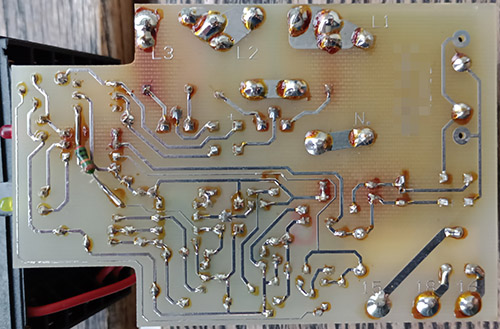
Last month’s ware is the Automatic AUT-450C “Connected Car Assistant” (OBD-II code scanner and GPS tracker with cellular, WiFi, and Bluetooth connectivity). The company went out of business shortly after the start of the pandemic.
Here’s some more views of the ware — I had left out some boards and views that made it a bit more challenging to identify, perhaps a bit too challenging.
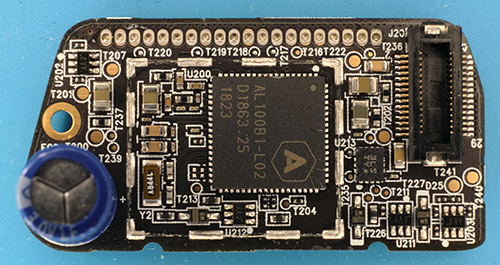
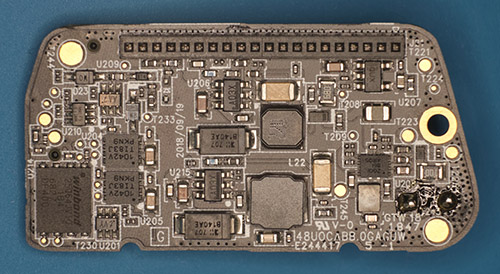
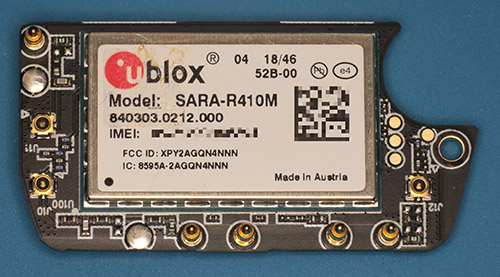
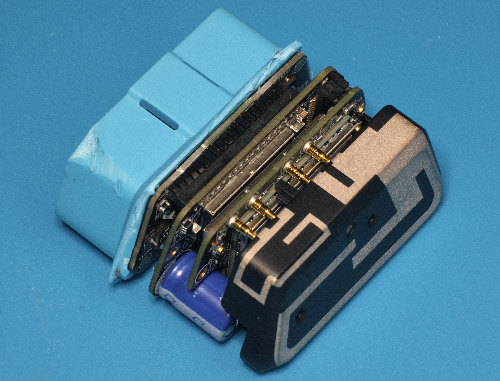
The hole cut-out that many assumed was a camera was actually a supercap — it is rated for 3.0V at 1F. Based on its direct connection to a switching regulator I’m guessing it’s there to coordinate safe shut-down of the SoC, and not for RTC maintenance.
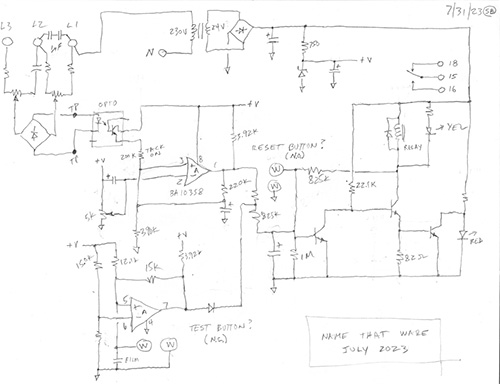
It’s a bit tough to pick a winner this month. Both Cody and Adrian shared detailed explanations, but I think overall Adrian might have gotten closest first, with a link to a fleet tracking device. I think the device is pretty close to what you’d have in a fleet tracker, but with a B2C business model instead of a B2B business model. Congrats Adrian, email me for your prize!